

pfSense is a utility based on FreeBSD. Its primary use is as a firewall but it is complex and we can do way more with it. Here I will go into detail concerning what I use it for, but there are many more things we can do with it, many funcionality that I don't use for now.
The first thing to know is that I actually have 2 pfSense computers running as a cluster. Each cluster member has a dedicated "SYNC" interface for syncing firewall states and rules, as well as configuration. A virtual IP address (VIP) is created using CARP for the LAN and WAN interface. My other machines use these VIP to access the firewall.
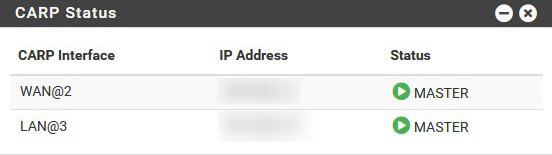
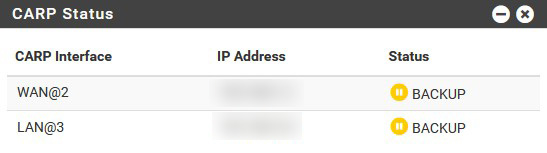
Thanks to that, when there is a failure of one of the firewalls, it is totally invisible for the other machines to know something went wrong, as the remaining firewall takes over and the VIPs are still reachable. As soon as the failing firewall comes back up, everything goes back to normal and this is invisible for the other machines as well.
My main use for this server is the firewall. It is installed on two dedicated physical machine which habe two gigabit network interfaces, and a dedicated SYNC interface as mentioned above. As for the other interfaces, one is plugged into my ISP router, which is the WAN side, and the other interface is plugged into a switch, which is the LAN side. Both are on a different subnet so the LAN is isolated from WAN, and everything that goes in or out is filtered with firewall rules. Concerning the LAN, each machine also has its own firewall, with everything blocked except for the connections the machines require.

By default, the system comes with some pre-defined rules, like refusing every incoming connection on the WAN interface. I can also add rules by myself.
On the action tab, a red cross means the traffic is being blocked, and a green validate icon means the traffic is authorized, and passes.
The interface corresponds to which interface the rule is being applied. When there is a right-pointing arrow, it means it is an outgoing connection from the interface. When there is no arrow, it is an incoming connection.
The rule tab displays the name of the rule. When it is a user-defined rule, there is a person icon next to the rule name.
The source and destination show the source IP and port, and destination IP and port. The protocol section tells us which protocol is used.
Regarding the firewall, I also installed a utility called pfblocker-ng, which is very similar to the well-known pi-hole.
It is a utility that creates a DNS hole which works with blacklisting and whitelisting. A list of URLs and IPs are present in these lists, and blocked ones are redirected via DNS to a VIP that leads to nowhere and acts like a black hole. As a consequence, the said URL is not resolved and cannot be displayed. When it's an IP, it is straight-up blocked.
This is very useful to block unwanted ads, spyware, malware and spamming sites and IP addresses. We can block incoming and outgoing connections.

There are multiple tabs here. There is the usual time and interface. The souce correspond to the device which initiated the blocked connection. The domain refers to the blocked URL, and feed group tells me which list has been used to block the connection.
It is possible to use as many lists as I want. A lot of them are available on github and other sites like this one. These feeds are created by the user in the pfblocker-ng configuration tab.
I also have an openvpn server configured on this machine. It allows me to connect remotely to my infrastructure when I'm not at home. It is very useful when I have to solve problems or just when I want to work on my projects when I'm not at home.
Each user needs to be created with a certificate. When authenticating, the user also has to enter a password in addition to the server verifying the validity of the certificate.

I can see the user who is connected, the time the connection was established, and also the real and virtual IPs of the user. I can kill the connection by clicking the cross on the right if I want someone to log out.
When using OpenVPN I noticed that my thoughput was not that great. It quickly became an issue when transferring larger files. As a result, I read online about what better options there were. A lot of people mentioned Wireguard, so I gave it a try. It works in a way similar to SSH : with private and public key. An optional but recommended shared passphrase can also be set.
After a tunnel is created, I can add peers to this tunnel. I chose to add each peer manually with a /32 address instead of a whole subnet for better security. A widget then tells me how many peers are connected, and the amount of data they transferred.
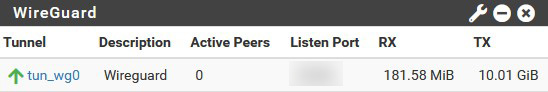
Now all my thoughput issues are solved so I'm still using Wireguard as my VPN to connect to my home network.
DHCP is a protocol that assign an IP address to a machine that asks for it. Usually it is done when a machine is powered on. It is also done when the lease is about to expire.
The lease time is defined by myself in the DHCP server's configuration. Usually, it is set to 24h, so when the server gives an IP to a machine, the machine has to ask again before it expires. If the machine is powered off and no new request is made, the DHCP server clears the lease so another machine can be assigned this IP address.
A lease is dynamic. For a same machine, different IP addresses can be assigned. The server will assign an IP that is in the range of IP to assign, which are also defined by myself in the configuration of the server. I can also add static leases, that means when a machine asks for an IP address, the server will always give it the same IP address. It's a reservation based on the MAC address of the network card.
In my current configuration, I have several static leases, and dynamic leases as well.

Like the firewall rules, static leases defined by myself have a user logo next to them. For dynamic leases, it's a validate sign.
For each lease I can see the IP address assigned by the server, the client mac address, hostname and description. The start and end sections define the start and end of the lease. There are none for static leases as the same IP will always be provided for the machines matching the MAC addresses. Here, the only dynamic lease is my desktop, and the lease duration is two hours.
If my desktop doesn't ask for a renewal, the IP will be cleared and available again. I also have the status of the machine, online or offline, lease type, and actions such as edit, wake on LAN, create static lease.
This machine also acts as an NTP server. It is used by other machines to have the correct time and date via network. The server synchronises itself with what is called NTP Pools, which give the exact time and date.

The pools have multiple machines linked to them so if a server from a pool is down, others can take the requests.
pfSense can generate certificate requests, private keys, and can also sign certificates. It then acts like a certificate authority. Thanks to that, I can create certificates for all my machines that have web interfaces.
I juste have to trust the certificate authority in my browser, and every web interface I access that has a certificate signed by this authority is trusted. This gets rid of the message saying "Your connection is not private" telling me the certificate authority can't be verified.
I can also generate certificates for services, like OpenVPN, and there is a certificate revocation list where I can revoke certificates.
